eBPF: Next-Gen Observability
eBPF (extended Berkeley Packet Filter) is transforming cloud-native observability by enabling in-kernel instrumentation. Without modifying your application code, you can leverage eBPF to monitor, trace, and profile applications at the kernel level, all with minimal overhead.
What is eBPF?
eBPF allows developers to run sandboxed programs in the Linux kernel without changing kernel source code or loading kernel modules. It's widely used for networking, performance profiling, and security. In observability, eBPF allows you to capture real-time metrics and logs directly from the kernel space, making it a powerful tool for understanding distributed system behavior.
Pixie and eBPF for Kubernetes Observability
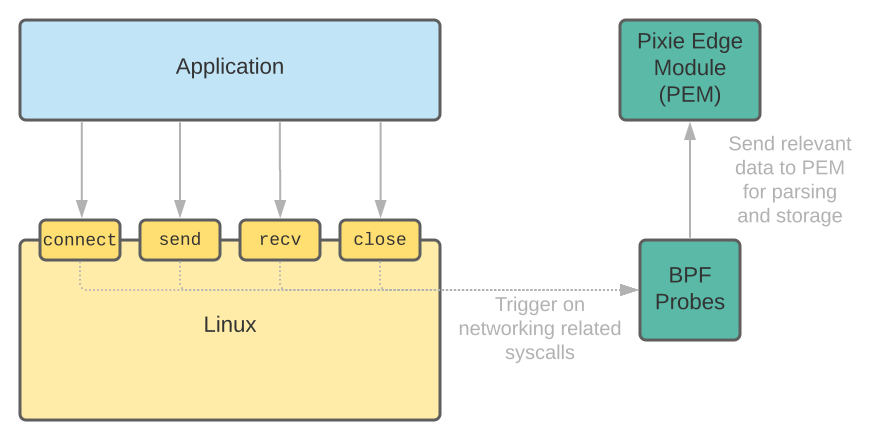
Pixie, a CNCF project, uses eBPF to autoinstrument Kubernetes clusters, allowing engineers to gather data on applications running in distributed environments without needing to inject sidecars or modify code. This helps simplify debugging and performance tuning.
By using eBPF, Pixie can trace system calls, network packets, and container activity at a granular level. Pixie's integration with eBPF allows you to automatically collect full-fidelity application and network data with zero instrumentation required from the user.
My Contributions to Pixie
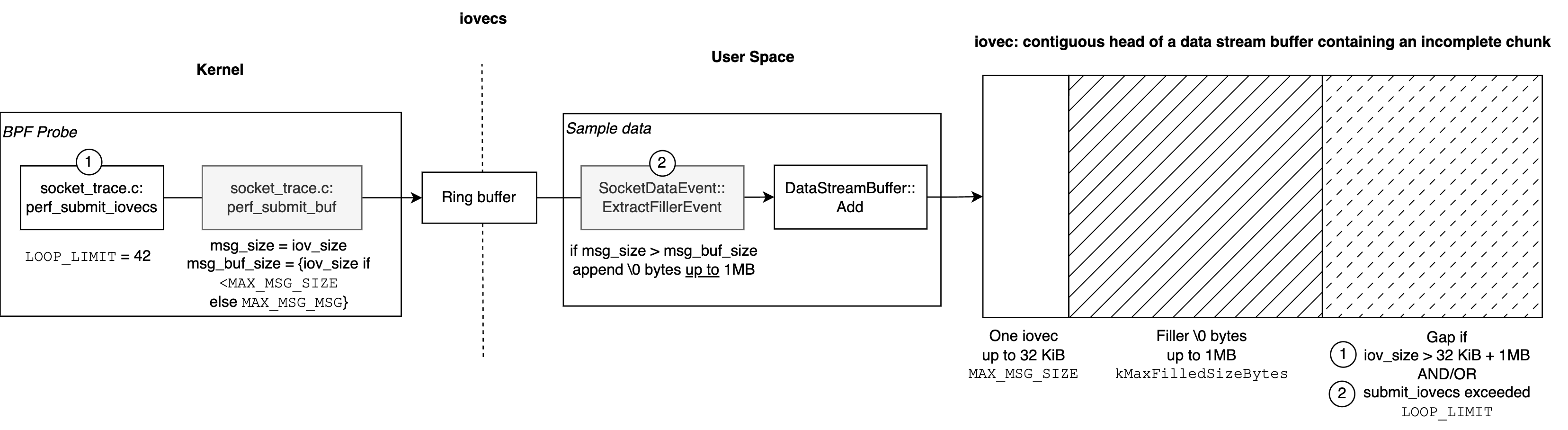
I have actively contributed to Pixie's open-source repository, focusing on performance optimizations and improving the efficiency of eBPF-based data collection. One notable contribution was addressing limitations in syscall tracing by dynamically adjusting loop limits for newer kernels, ensuring more complete syscall capture.
Additionally, I helped develop an experimental lazy parsing mechanism for Pixie's HTTP protocol parser to better handle partial frames, improving the observability of distributed applications in real-time. For more information, see this github issue.